Locking Down Your Cloud Network: The Basics
How to avoid exposing your enterprise network to the internet and other cloud network security best practices.
As they quickly adopted cloud infrastructure services over the last decade, companies have been deploying new workloads more and more frequently. The availability of cloud services has simplified the deployment process. Because of the rapid deployment, it's easy for cloud network security to take a back seat as previously on-premises applications and services are migrated from data centers to the cloud.
Cloud services are by default connected to the internet, creating new challenges for securing workloads and data against threats from hacking groups and from trusted insiders. As more users work remotely and access services from outside the enterprise network, you may not know whether you're leaving your cloud environment vulnerable.
Some organizations mistakenly assume that cloud service providers carry the burden of network security in the cloud environment. By default, providers implement network security measures to protect their cloud hosting infrastructure, leaving to users the responsibility of securing their workloads. Without proper measures to secure your cloud network, your workloads may be accessible from the enterprise network and the internet alike.
In addition, many organizations must adhere to regulatory standards (such as HIPAA, FedRAMP and GDPR) to guarantee the correct management of sensitive data. Cloud network security plays an important role in their ability to comply with those regulations.
This guide will cover best practices and techniques for improving cloud network security to fortify your cloud environment, enhance regulatory compliance and as a result minimize risk.
Cloud Network Security Best Practices
Cloud security best practices start with knowing which aspects of security are your responsibility and which are your provider's. Then, look at ways to limit access to your traffic: by establishing secure cloud connectivity, using a zero-trust model and tightening access to your public-facing applications.
Understand the Shared Responsibility Model
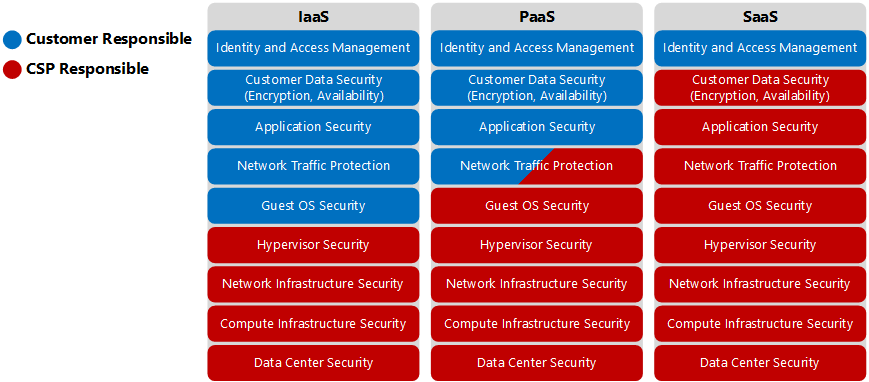
In a cloud environment, the cloud service provider (CSP) hosts resources on behalf of the customer while offering different levels of control over its cloud services. Consequently, security responsibilities are shared between the CSP and the customer. The CSP is responsible for the security of the cloud infrastructure, while the customer is responsible for the security of their data and applications and for managing access to their cloud services. A clear understanding of the CSP’s and the customer’s respective areas of responsibility is critical in ensuring effective and comprehensive security controls.
The following diagram illustrates the sharing of security responsibilities between the CSP and the customer across the typical cloud service categories of infrastructure as a service (IaaS), platform as a service (PaaS) and software as a service (SaaS):
Securely Connect Your Enterprise Network to Your Cloud Service Provider
If you're connecting your enterprise network to a cloud provider, make sure that connection is secure. It’s recommended to use a VPN. If connecting over the internet is the only option, the best practices include encrypting all traffic, putting a firewall in front of the enterprise network and using web and TLS proxies.
Administering and consuming enterprise workloads over the public internet, however, may leave your network vulnerable and require significant risk management. Some cloud services' storage containers or databases are also available over the internet by default. If your cloud service provider offers these services using a private cloud network for access, you can reduce the risk.
For maximum security, it’s possible to connect privately over a dedicated connection, bypassing the internet. All major cloud providers offer this “cloud onramp” option, available to tenants in colocation data centers that host the onramps (AWS Direct Connect, Azure ExpressRoute, Oracle FastConnect, Google Cloud Interconnect). Equinix hosts more onramps than any other operator, while Equinix dedicated cloud users can launch and manage private connections to clouds on a global basis remotely and virtually, including through common Infrastructure-as-Code tools. (In addition to the security benefit, private connections are reliably fast and offer dedicated bandwidth and low latency.)
The most secure solutions use encryption or dynamic traffic tunneling over dedicated cross connects to ensure sensitive data is encrypted in transit and protected from the cloud provider.
Implement a Zero-Trust Networking Model
Traditional perimeter-based secure networking models, which assume all users or services inside the perimeter are trustworthy, are insufficient against today's cyberthreats. With zero-trust networking (ZTN), nothing and no one, whether internal or external, is trusted by default.
Underlying a ZTN security model is a system of identity verification, access management and continuous monitoring to ensure that only identified, authorized entities are provided access exactly to the resources they require and nothing else, applying the principle of least privilege at the network layer. This is enabled by technologies like multifactor authentication (MFA), posture checking, continuous security monitoring and granular access controls (role based and, if available, attribute based).
A ZTN security model not only prevents unauthorized access, but it also detects anomalies, provides enhanced visibility into who and what is accessing services and mitigates the impact of a breach by limiting the access of any one entity. Adopting a ZTN model can go a long way in reducing the risk of data breaches and other unauthorized access.
Secure Internet-Facing Services
Applications consumed over the internet are a primary target for cyberthreats. To secure an application that's exposed to the internet, you can implement a web application firewall (WAF) to protect against intrusions using HTTP traffic.
WAFs act as the mediator between applications and the internet. They filter requests to mitigate DDoS attacks and monitor client-server traffic to detect and prevent common attack types, such as cross-site scripting (XSS), SQL injection and remote command execution. Options for WAF deployment include cloud-native offerings from cloud service providers or network virtual appliance (NVA) WAFs from your preferred network security vendor.
When you set up a WAF for your application, configure it so that only essential UDP and TCP ports are open. Cyberthreats constantly scan the internet for open ports to find potential targets, so blocking ports that aren't required or secured is a simple yet effective way to protect your cloud network infrastructure. Additionally, implementing a threat detection system using Intrusion Detection System (IDS) and Security Information and Event Management (SIEM) solutions can assist in logging activity and alerting when a potential attack is underway.
Implement Cloud Network Microsegmentation
Traditional network segmentation involves dividing the network into workload- or organization-based segments and policing connectivity between them. Cloud providers, which use virtualization for cloud infrastructure, enable more granular modes of segmentation using software-defined policies. Commonly referred to as microsegmentation, this strategy divides a cloud network into smaller isolated segments to restrict lateral movement. This measure adds an extra layer of security by compartmentalizing workloads and only allowing essential flows between nodes in a segment.
Implement a Good Identity and Access Management System
Having an effective identity and access management (IAM) system in place is crucial for managing user identities and provisioning authenticated access to resources. Good IAM systems not only facilitate user onboarding and provisioning but also handle offboarding and deprovisioning using automated processes.
Additionally, automatically granting and revoking access based on organizational changes reduces the risk of excessive permission allocation. Advanced IAM systems (such as Microsoft Entra ID, JumpCloud and Okta) offer integration with human-resources applications to streamline HR and IT operations by ensuring resource permissions are correct.
Use Role-Based Access Control
A discriminatory role-based access control (RBAC) model that restricts resource access based on user roles and attributes helps ensure that users have the necessary access to the data and resources required for their position.
Modern RBAC solutions replace the traditional RBAC approach, which relies on static roles, with access control that uses dynamic roles, adjusting access in real time based on factors like login time, location and behavior. For example, traditional RBAC might allow a user with sufficient role-based permissions to access a cloud service from an unusual location at an unusual time, while dynamic RBAC would recognize the anomaly in user behavior and deny access. This builds upon the principle of least privilege by accounting for access conditions that fall outside the typical use cases of a user's role. Using RBAC in this way improves responsiveness and reduces the security risk if a user is compromised.
Encrypt Data at Rest and Data in Transit
Data being sent to the cloud should always be encrypted to mitigate unauthorized access and data breaches. Data at rest and in transit should use modern encryption in accordance with the latest standards.
You can gain an additional layer of security and tamper resistance by encrypting cloud-stored data with hardware security module (HSM) keys.
Have a Robust Key Management Framework
Selecting a secure key management system (KMS) is crucial in securing cryptographic keys used for encrypting and decrypting sensitive data. A good KMS will provide key rotation, secure storage, access controls and auditing capabilities. Take advantage of your cloud environment to geographically distribute your KMS infrastructure to ensure redundancy and continuous availability in the case of regional outages.
Use a Security Monitoring System
A security monitoring system lets you identify and respond to security events across cloud and on-premises networks. Threat intelligence feeds provide information on emerging cyberthreats, accelerating recognition of new exploits.
Centralizing and analyzing logs in the security monitoring system provides visibility of all security-related activity and informs proactive security measures. Mature organizations should assess their environment with penetration testing, using the opportunity to tease out any weaknesses in their security posture and monitoring systems.
Have a Security Incident Response Plan
Finally, take a proactive approach to security incidents with a well-documented and rehearsed security incident response plan. All organizations should have a plan in case the security measures in place don't prevent an incident. This plan should identify the responsibilities of all personnel and include steps for containment, eradication, recovery and analysis once the incident is over.
Businesses that rely on cloud services can be left open to threats as they adopt a new network model, one without the implicit protections of a traditional on-premises network. Cloud network security is essential to safeguard against emerging threats and provide the confidence needed to consume cloud services at scale.
Adopting best-practice security measures such as secure enterprise connectivity, zero-trust networking, protecting internet-facing services, microsegmentation and understanding the shared responsibility model will help mitigate cyber risk. Taking additional steps, like advanced IAM, dynamic RBAC, strong encryption, secure key management, security monitoring and incident response planning, will greatly improve your overall cloud network security posture.
Once you’ve implemented security measures, invest the time and capital necessary to stay informed about emerging threats, technological developments and changes to regulatory requirements. The measures detailed here serve as foundational principles to navigate the cloud journey safely and successfully.

Ready to kick the tires?
Use code DEPLOYNOW for $300 credit