- Home /
- Resources /
- Learning center /
- Configuring Okta f...
Configuring Okta for Equinix Federated SSO
Learn how to manage users automatically from your Okta user directory

On this page
Integrating services with Identity Providers (IdPs) has become an industry best practice for businesses seeking to optimize their security posture and streamline user access management. Equinix support for SAML-based SSO (using your own IdP to login to Equinix) is generally available, and to accompany it, we are happy to announce a beta release of the newest feature of our identity platform - support for SCIM-based user provisioning and deprovisioning. This means that your IdP will not just be a part of the login flow, but will be directly responsible for creating and removing Equinix user accounts.
Automating user management comes with several benefits for your business - including a streamlined experience, reduced IT burden, reduced rate of mistakes, and increased ability to enforce compliance with security policies. This guide will walk you through automating user provisioning in Equinix with Okta using the SCIM protocol.
Prerequisites
This guide assumes you have completed SSO onboarding at the Equinix Federated SSO site. The SSO onboarding process will provide you with an integration URL and token, which will be referenced in this guide.
Creating the Application
The provisioner will be configured using an Okta Application. To configure this, open the Okta admin console and select Applications in the sidebar. Click Browse App Catalog. While in beta, Equinix's SCIM service is not integrated with the Equinix Customer Portal catalog application, so search for "Governance with SCIM" and select (OAuth Bearer Token) Governance with SCIM 2.0 and Add Integration.
The app can be named anything that reasonably identifies it, such as "Equinix" or "Equinix Provisioning." Under Sign-On Options, the SAML fields for this SCIM application may be filled in if this application will also be used for the login flow, but Application username format under Credentials Details must be set to "Email" (and if a different Okta Application is used for SAML SSO to Equinix, that one must be "Email" as well). Click Done to create the application.
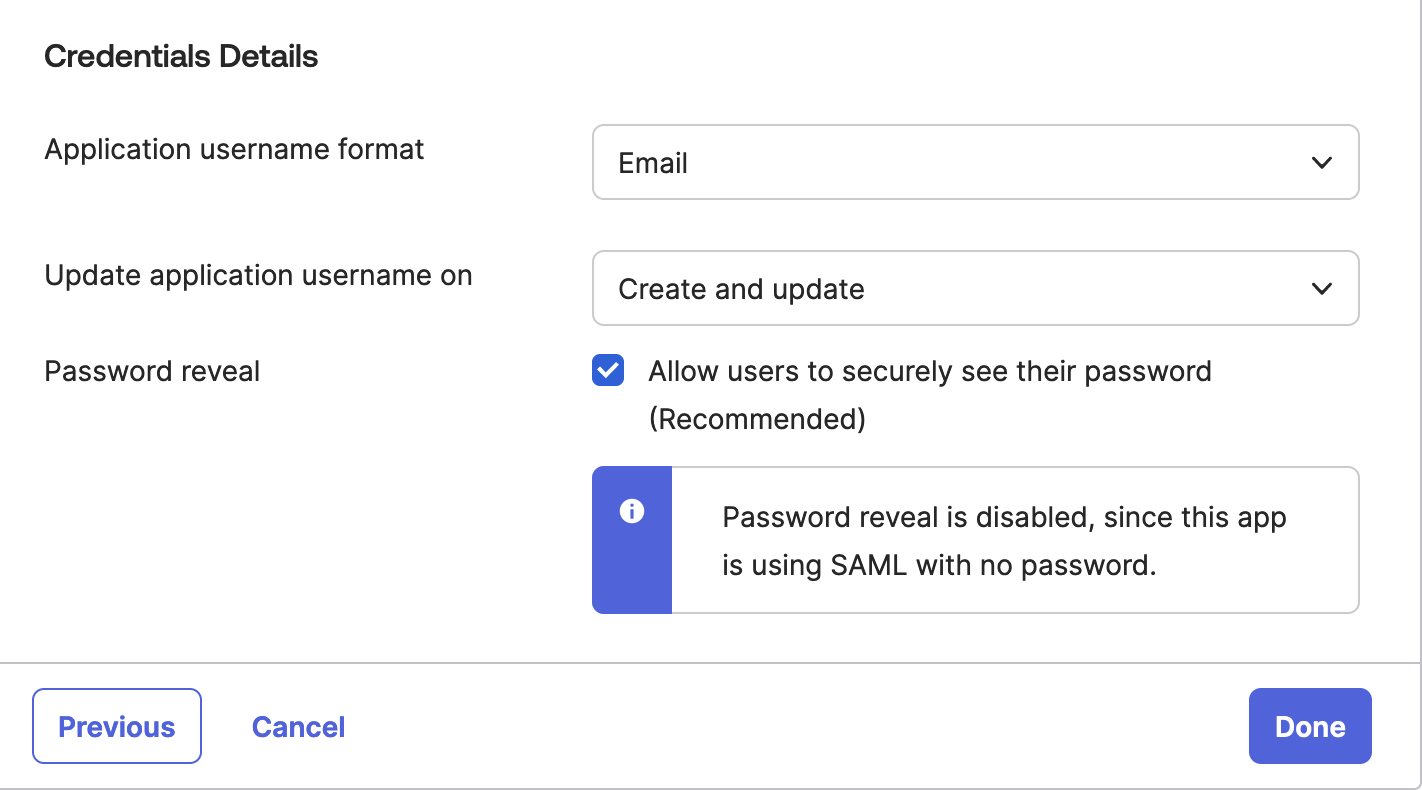
Configuring Provisioning
Once the application has been created, Okta will take you to the application's management panel. Open the Provisioning section in the tab bar and click Configure API Integration. Enter the URL and token provided to you by federation.equinix.com, and test the credentials. Save the changes.
Note: Equinix's SCIM service does not support group functionality at this time, but plans to in the future. If you'd like Equinix groups to be reflected in Okta, you may enable the Import Groups function.
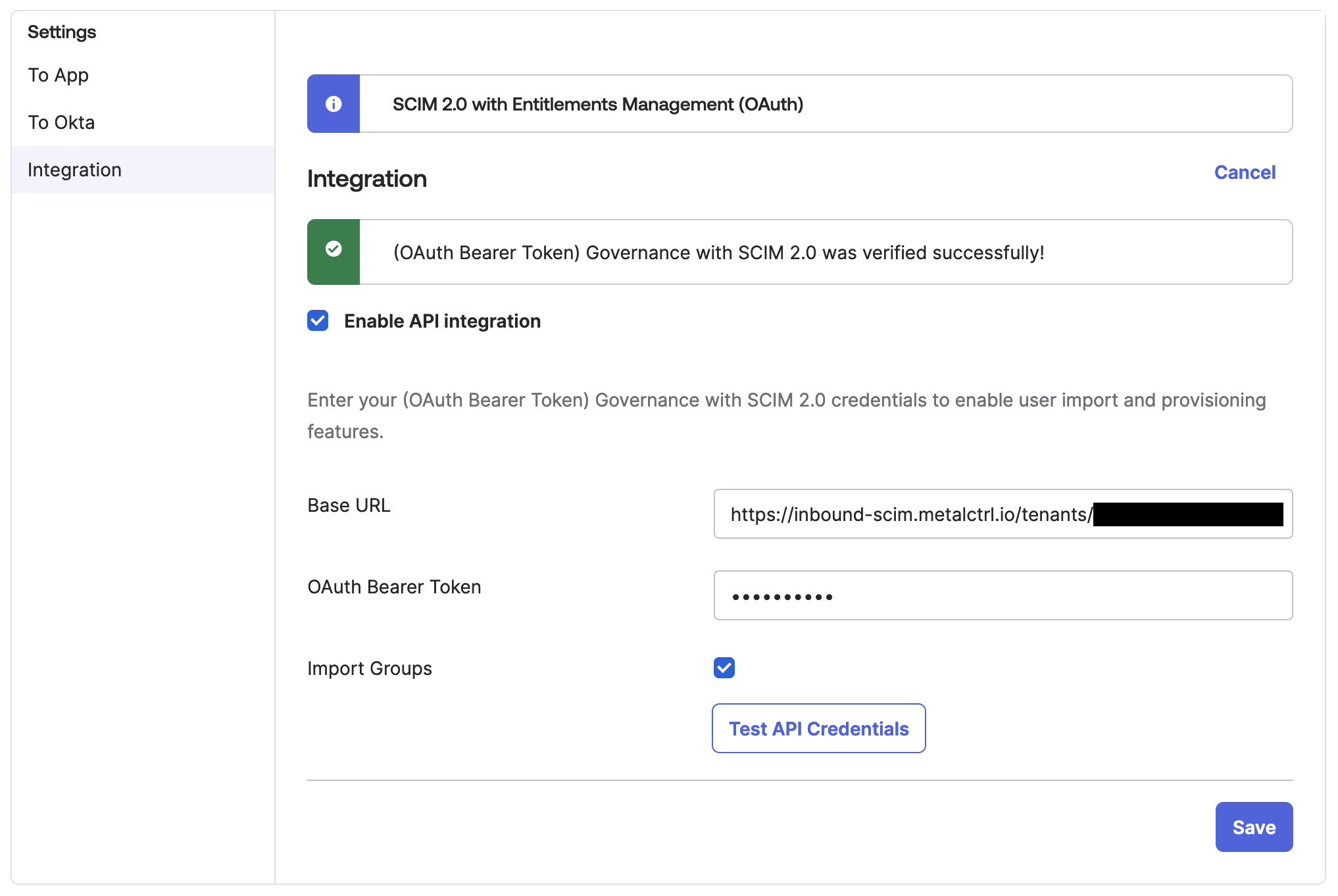
Enabling Provisioning
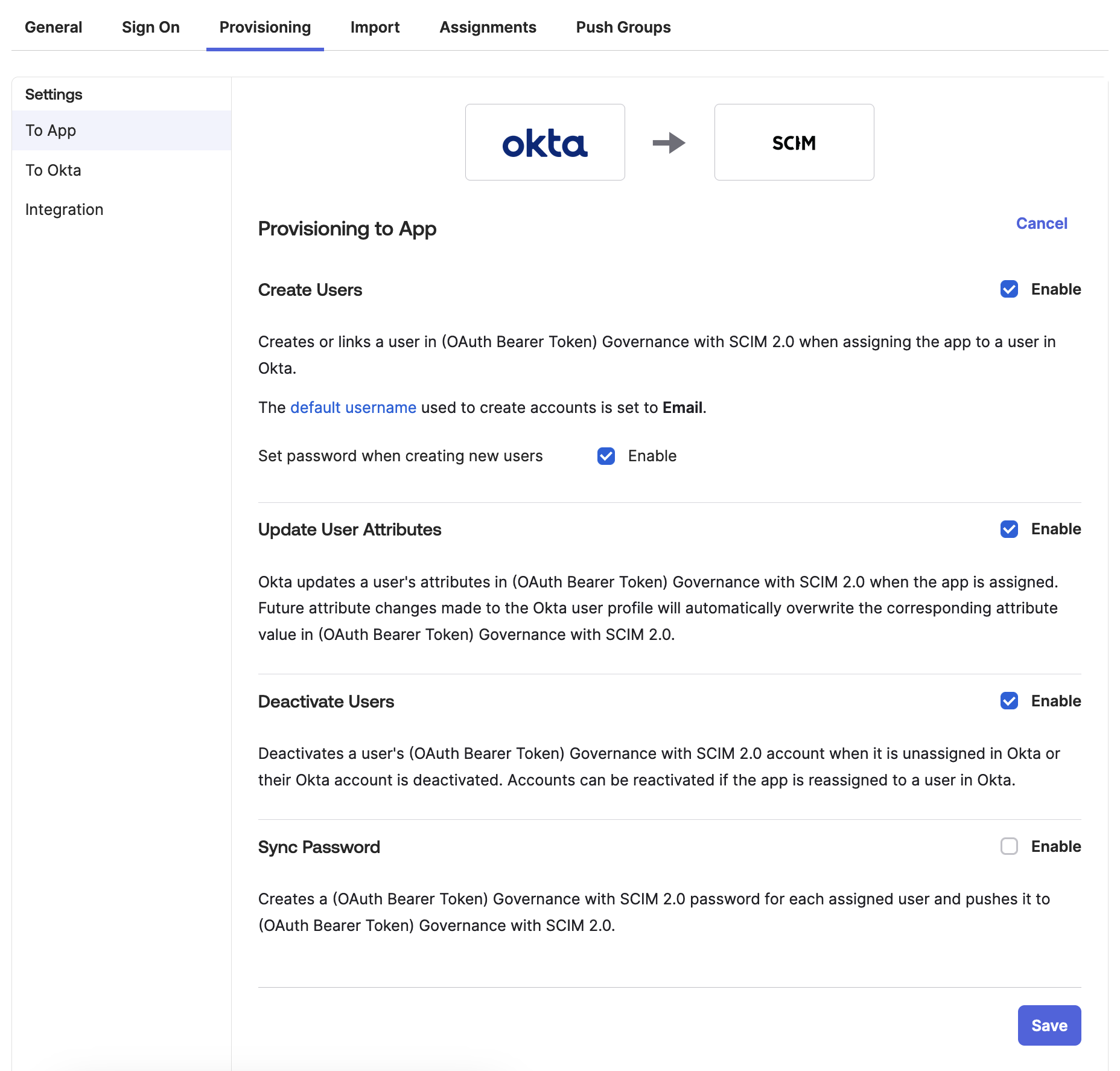
With the credentials in place, return to the Provisioning tab, and select To App. Click Edit to make the checkboxes editable, and switch on Create Users, Update User Attributes, and Deactivate Users. Ensure that the default username is Email.
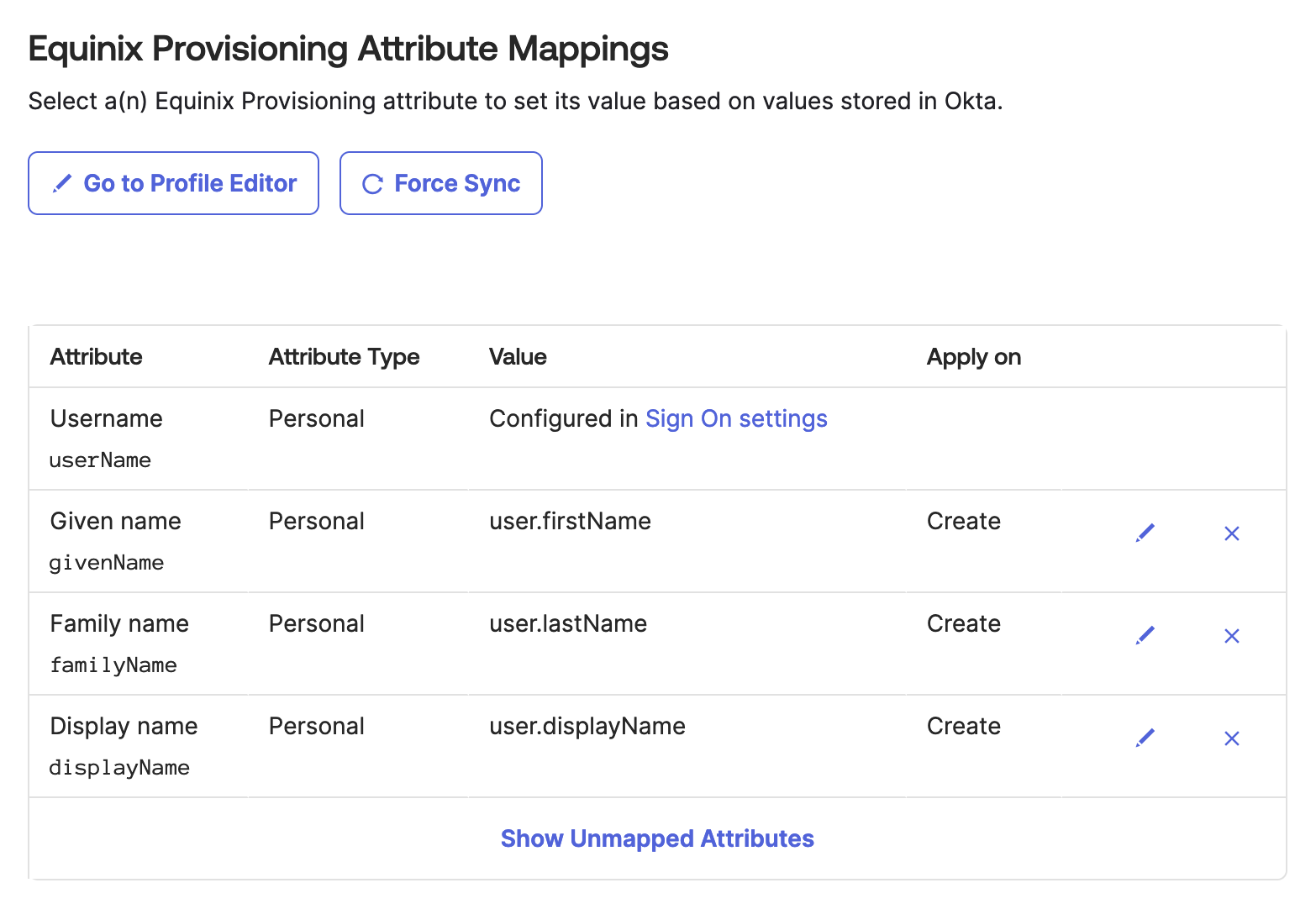
Configuring Attribute Mappings
Continuing under the To App section, configure the mappings of Okta attributes to Equinix user attributes. Configure the mappings as shown:
| Attribute | Attribute Type | Value | Apply on |
|---|---|---|---|
| userName | Personal | Configured in Sign On settings | |
| givenName | Personal | user.firstName | Create and Update |
| familyName | Personal | user.lastName | Create and Update |
| displayName | Personal | user.displayName | Create and Update |
| primaryPhone | Personal | user.primaryPhone | Create and Update |
| primaryPhoneType | Personal | "work" | Create and Update |
| locale | Group | user.locale | Create and Update |
Note that primaryPhoneType is set to work by selecting "Same value for all users".
Additional default mappings should be deleted or unmapped.
Adding Users and Groups For Provisioning
Users can be assigned to the application for provisioning either individually or by group. Open the Assignments tab and click the Assign button to add users to the application. Okta should begin provisioning the users in Equinix immediately.
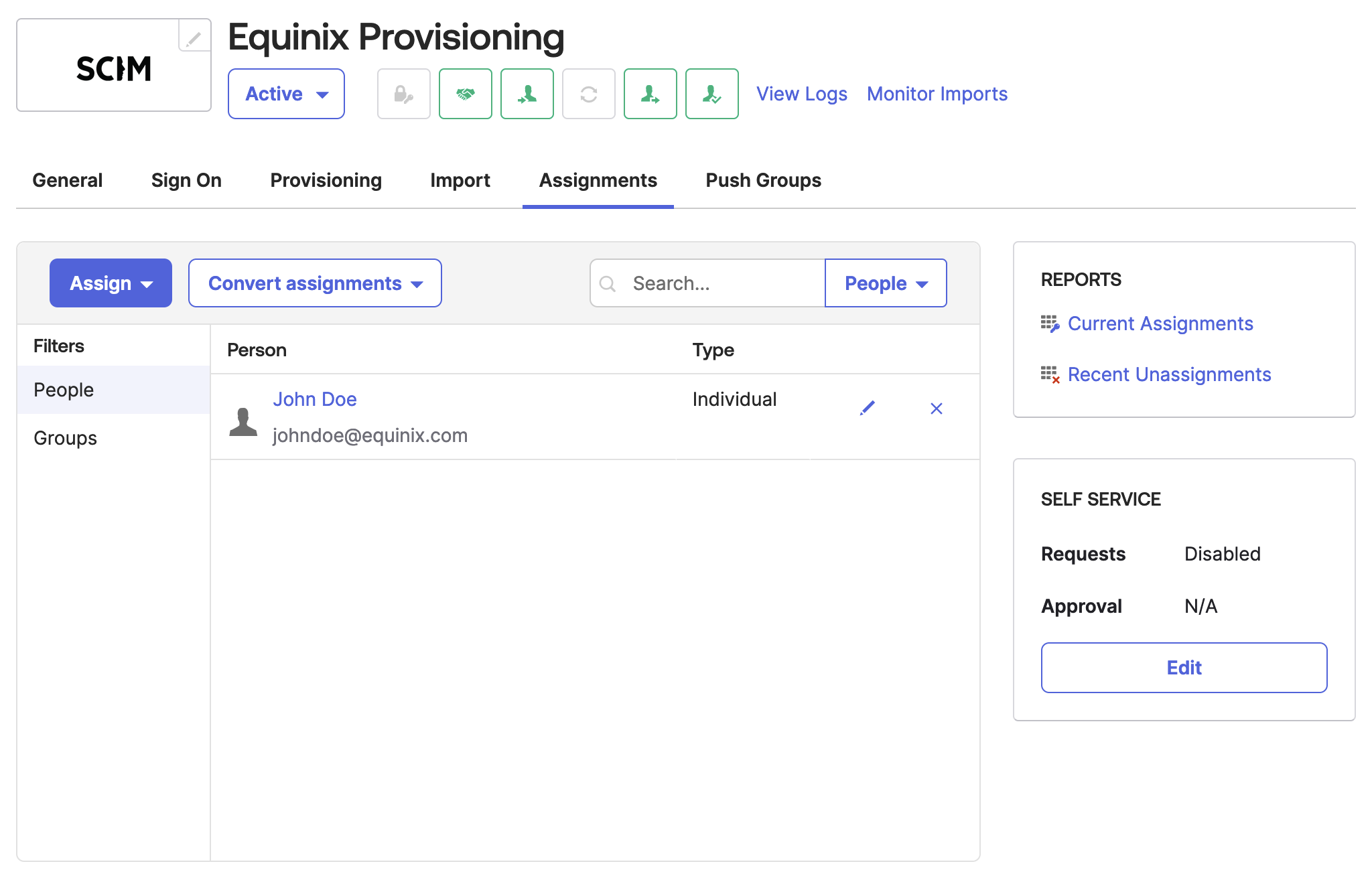
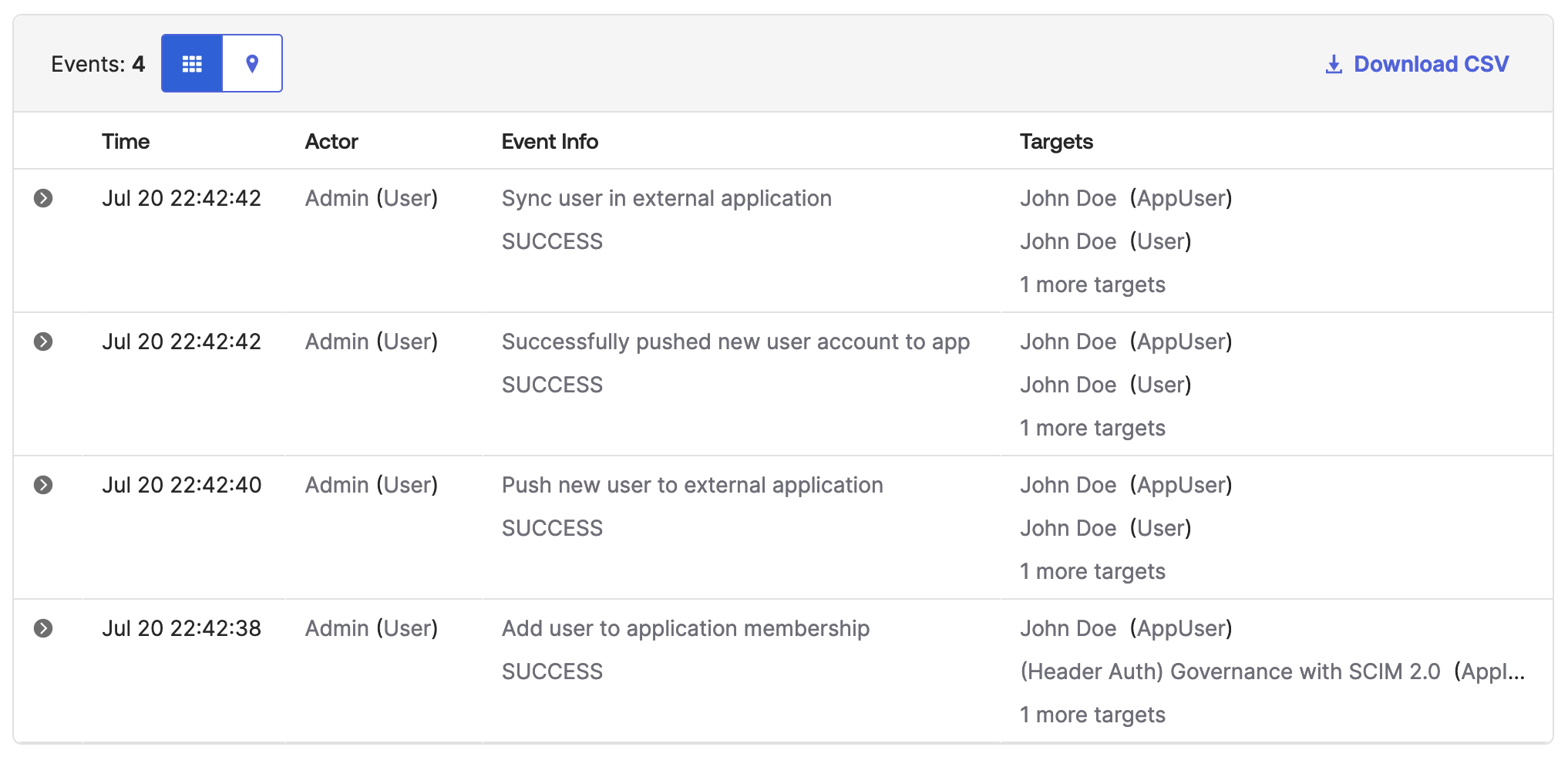
Verifing Successful Provisioning
At this point, Okta should have all of the configuration necessary to provision and deprovision users in Equinix. Click View Logs next to the application's name in the header, or navigate to Reports, System Log to see provisioning events. It is a good idea to monitor the first provision after setup to ensure that the connection is working smoothly.
Conclusion
You've configured Okta to automate your user management tasks with the SCIM protocol. This will streamline your login flow, and enhance security by keeping the identity management within the identity provider.
Last updated
07 January, 2025Category
Tagged
TechnicalYou may also like
Dig deeper into similar topics in our archives
Crosscloud VPN with WireGuard
Learn to establish secure VPN connections across cloud environments using WireGuard, including detailed setups for site-to-site tunnels and VPN gateways with NAT on Equinix Metal, enhancing...
Kubernetes Cluster API
Learn how to provision a Kubernetes cluster with Cluster API
Kubernetes with kubeadm
Learn how to deploy Kubernetes with kubeadm using userdata

OpenStack DevStack
Use DevStack to install and test OpenStack on an Equinix Metal server.