How to Use BGP Flowspec as Your Network’s Smart DDoS Shield
Flowspec uses BGP as the carrier for DDoS mitigation policies and the upstream service provider's network to enforce them at the edge.

For about one month starting in early September 2024, hackers used unsecured connected devices all around the world to launch a massive DDoS campaign aimed at disrupting companies in the financial, telecommunications and internet services industries, among others, according to Cloudflare.
Assembled out of a variety of compromised devices, from home internet routers and DVRs to web servers, the massive botnet sent junk traffic across the internet at rates unprecedented among publicly disclosed DDoS attacks, Cloudflare, whose system mitigated the onslaught, said. The two largest attacks in the campaign aimed at a single Cloudflare customer: one at 3.8 terabits per second and the other at 2.14 billion packets per second.
Attackers taking advantage of the proliferation of cheap, poorly secured connected devices to launch bigger and bigger DDoS attacks has been an ongoing problem for years, and, judging by recent reports like Cloudflare’s, continues to grow in scale.
DDoS attacks are effective because they overwhelm the capacity of a system to service the traffic being sent to it. One effective technique for countering an attack uses BGP Flowspec (Flow Specification), a networking technology that propagates filtering rules targeting the junk traffic via BGP route advertisements. The Internet Engineering Task Force (IETF) published the latest iteration of BGP Flowspec in RFC 8955 in 2020, and it has proven to be a powerful DDoS mitigation tool.
In contrast with traditional DDoS mitigation methods, which require the organization under attack to filter DDoS traffic, Flowspec uses BGP as the carrier for DDoS mitigation policies and the upstream service provider's network to enforce them. This is a better approach than the traditional methods that rely on payload inspection, manual filtering configuration or traffic engineering, each of which lacks scalability and can impact performance.
More on BGP:
- How BGP Selects the Best Route for Your Packets
- BGP Hijacking and How to Guard Against It
- BGP Confederations vs. Route Reflectors and How to Choose the Right One
In this article, we will explain how BGP Flowspec dynamically propagates DDoS mitigation policies across the network and how you can create granular traffic filtering rules to focus on DDoS traffic without impeding legitimate traffic.
The Role of BGP Flowspec in DDoS Mitigation
BGP Flowspec extends BGP update messages to include additional fields that specify criteria to identify DDoS traffic flows and actions that apply to them. Its use cases reside at the enterprise edge, where you can use BGP Flowspec to inform your service provider of the offending traffic patterns and use your provider's network infrastructure to mitigate the attack.
Volumetric DDoS attacks surge the target system at Layers 3 and 4 with the intent of disabling or denying it. This is where BGP Flowspec can excel, as it uses packet header information to filter DDoS traffic on the service provider's network. This can forward and filter traffic at much higher rates than most organizations can, giving you far more filtering capacity than you would normally have.
Conversely, low-and-slow DDoS attacks wear away at an application's resources without requiring large volumes of traffic. These attacks are more likely to go undetected because they're difficult to distinguish from legitimate traffic. BGP Flowspec cannot mitigate low-and-slow attacks, because they target systems using protocols above Layer 4.
Traditional volumetric DDoS mitigation tools like remotely triggered black hole (RTBH) and access control lists (ACLs) each carry deficiencies that make them unsuitable for modern defenses. RTBH gives the service provider a discard route (i.e. a route with a next-hop to nowhere, discarding the traffic) for the threatened system, which thwarts the attack. However, by preventing all access to the system, RTBH, in a way, achieves the goal of the DDoS attack, making it unsuitable in most scenarios. ACLs require the organization under attack to contact its service provider to configure the necessary filters to mitigate the attack manually, which is not very efficient or scalable when time is of the essence. In contrast, BGP Flowspec allows for rapid response to volumetric DDoS attacks, with automatic propagation of granular traffic filters for service providers to enforce using their high-capacity networks.
How to Use BGP Flowspec to Mitigate DDoS Attacks
You can implement BGP Flowspec provided you have a BGP connection to your service provider's network and your edge router supports BGP Flowspec. The Flowspec filter rules you configure are included in the BGP route advertisement for the relevant prefix. A prerequisite is contacting your service provider and ensure it will enable BGP Flowspec for your upstream service. Otherwise, your Flowspec filter rules may not be enforced.
BGP Flowspec Implementation
If you've established that you can deploy BGP Flowspec, you can configure your edge device to send filtering rules along with the public prefixes you already advertise to your service provider. Don't forget that Flowspec requires you to manually configure the filtering rules you wish to enforce, and it automatically propagates those rules to your service provider. Here’s how BGP Flowspec achieves this:
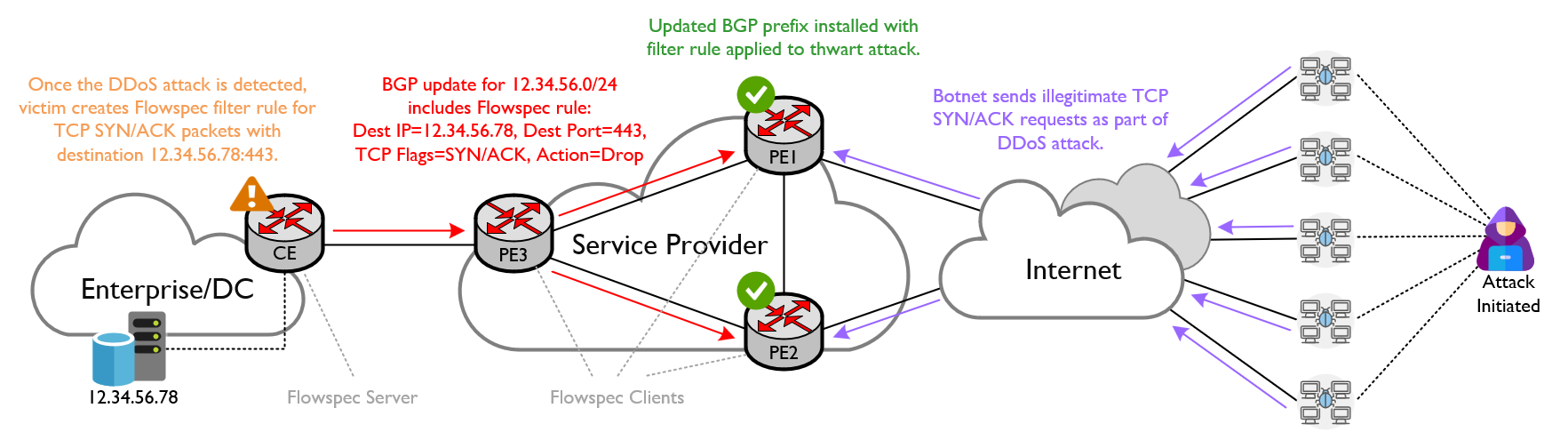
- When a DDoS attack is detected, you need to identify the traffic flows contributing to the attack.
- Separate systems are required to detect and analyze a DDoS attack before you can use Flowspec to mitigate it, including network traffic monitors, intrusion detection systems (IDSs) and security information and event management (SIEM) systems.
- Once you understand the pattern of the DDoS traffic, you can configure a Flowspec filter rule on your edge router (the Flowspec server) that specifies the matching criteria for a traffic flow with the resulting action and applies it to the associated BGP route.
- When your service provider receives a route with Flowspec information, the route is propagated across the service provider's BGP network, including Flowspec attributes, and the corresponding filter rule is installed by each router (the Flowspec clients).
- Once the offending DDoS traffic hits the service provider's network, the configured filter action is applied to each packet (e.g. dropped, throttled, redirected, etc.), and the attack is halted.
The diagram below illustrates the conceptual operation of BGP Flowspec in response to a DDoS attack:
BGP Flowspec Attributes
When you configure a Flowspec rule on your edge router, BGP includes additional Network Layer Reachability Information (NLRI) and BGP extended communities in the associated route advertisement, encoded with the values required to apply your filter rule.
Flowspec's NLRI provides granular options for defining the traffic flows you wish to target while avoiding legitimate traffic. Here are the NLRI type values BGP Flowspec uses to identify DDoS traffic flows:
|
Type Value |
Name |
Description |
|---|---|---|
|
1 |
Destination Prefix |
Target IP address or subnet |
|
2 |
Source Prefix |
Originating IP address or subnet |
|
3 |
IP Protocol |
Protocol type, including TCP, UDP and ICMP |
|
4 |
Port |
Port number belonging to the source or destination |
|
5 |
Destination Port |
Port number the traffic is targeting |
|
6 |
Source Port |
Port number that originated the traffic |
|
7 |
ICMP Type |
Type of message for ICMP packets |
|
8 |
ICMP Code |
Code specified within an ICMP packet |
|
9 |
TCP Flags |
TCP connection state (SYN, ACK, FIN, RST, etc.) |
|
10 |
Packet Length |
Length of the IP packet in bits |
|
11 |
DSCP |
Type of service |
|
12 |
Fragment Encoding |
Payload fragmentation notifier |
Flowspec's BGP extended communities provide several options for handling DDoS traffic to mitigate attacks. This table details the BGP extended community values (in hexadecimal format) and the encoded actions that are applied to DDoS traffic flows:
|
BGP Community |
Action |
Description |
|---|---|---|
|
0x8006 |
traffic-rate-bytes |
Throttles traffic rate in bytes per second |
|
0x800c |
traffic-rate-packets |
Throttles traffic rate in packets per second |
|
0x8007 |
traffic-action |
Specifies whether to drop or log the traffic or continue evaluating the filter |
|
0x8008 |
rt-redirect |
Redirects the traffic to a virtual routing and forwarding (VRF) instance with the specified route target |
|
0x8009 |
traffic-marking |
Marks the traffic with the specified differentiated services code point (DSCP) value for quality of service (QOS) applications |
So, what happens if you configure multiple Flowspec rules for a prefix, and how will BGP know which one to apply if a traffic flow matches multiple rules? BGP Flowspec compares the type values of each rule, preferring the rule with the lowest type value. That means if DDoS traffic matches two Flowspec rules, but one rule uses type 2 NLRI (source prefix) while the other uses type 6 NLRI (source port), the rule with the lowest type value (2) will be applied.
Configuring BGP Flowspec
Let's configure an example BGP Flowspec rule to demonstrate how you can implement it to mitigate a DDoS attack. In this scenario, your security operations center (SOC) has used its monitoring systems to identify a DDoS attack targeting a web server (hosted at 12.34.56.78/32) from thousands of IP addresses using a TCP SYN/ACK flood. A TCP SYN/ACK flood seeks to occupy the server by matching SYN/ACK responses with nonexistent SYN requests, while legitimate requests go unhandled and time out.
You can mitigate this DDoS attack by dropping any TCP SYN/ACK packets destined for the web server, as it's irregular for servers to receive this type of TCP packet from clients. In addition, you can specify the destination IP of the web server and the port that traffic is targeting. Applying a Flowspec filter using these criteria will reduce the likelihood that legitimate traffic is impacted by DDoS mitigation. This example uses the configuration for a Cisco IOS-XR-based router, but you can follow the steps specific to your vendor's implementation.
First, define the traffic you want to filter using a class map. Note that the TCP flag combination is provided in hexadecimal format in this example. SYN is 0x02 and ACK is 0x10, which together equal 0x12 (representing an SYN/ACK packet):
class-map type traffic match-all SYN-ACK-FLOOD
match destination-address ipv4 12.34.56.78 255.255.255.255
match protocol tcp
match tcp-flag 0x12
match destination-port 443
end-class-map
!
Next, assign an action to the DDoS traffic using a policy map:
policy-map type pbr DROP-SYN-ACK
class type traffic SYN-ACK-FLOOD
drop
!
class type traffic class-default
!
end-policy-map
!
Initialize BGP Flowspec and enable it for the BGP neighbor connection to the service provider:
router bgp 65001
address-family ipv4 flowspec
!
neighbor 123.4.5.6
address-family ipv4 flowspec
!
Finally, assign the policy map to the Flowspec configuration:
flowspec
address-family ipv4
service-policy type pbr DROP-SYN-ACK
!
At this point, BGP automatically propagates the rule to its neighbors using BGP update messages. To verify that the Flowspec filter rule is active, you can run a query command like this and observe a similar output:
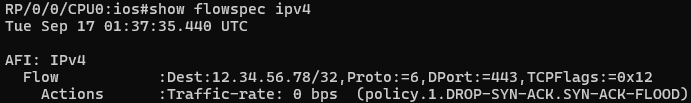
You can see how deploying Flowspec from the edge of your network provides rapid mitigation to DDoS attacks, as the filter rule propagates to your service provider's network and uses its filtering resources instead of your own.
Conclusion
BGP Flowspec provides real-time mitigation for DDoS attacks by propagating filter rules to your service provider's network for enforcement. Flowspec is a powerful tool for addressing volumetric DDoS attacks due to its granular control over traffic flows using Layer 3 and 4 header information. However, it does nothing to prevent low-and-slow DDoS attacks from disabling your applications. Remember to engage with your service provider when considering BGP Flowspec to ensure your requirements will be met.
If your organization requires full control of BGP routing on its network, Equinix offers a lot of flexibility in configuring BGP globally, both for private bare metal compute and storage and for connectivity to network operators, cloud providers and enterprises.