BGP Hijacking and How to Guard Against It
It’s not a new or particularly sophisticated attack method, but it remains quite effective and devastating for the victim.

In January 2024, a large European mobile carrier fell victim to a Border Gateway Protocol (BGP) hijack, which compromised its Regional Internet Registry for Europe, Middle East and Central Asia (RIPE) account, and suffered several hours of network service disruptions. The RIPE investigation discovered that the attacker relied on a malware infection from late 2023 that had captured passwords, including a distressingly simple password for the RIPE account. Because the victim hadn't yet implemented multifactor authentication (MFA), the BGP hijacking was relatively simple to pull off.
Unfortunately, BGP hijacking remains a persistent threat, and the motives behind it differ greatly. Some attackers do it for amusement, while others are part of a larger, ongoing campaign. Beyond reputational damage, these attacks allow criminals to capture traffic intended for other organizations. Even if the data is encrypted, advanced persistent threat (APT) actors may be patient enough to wait to uncover vulnerabilities in encryption algorithms or for stolen keys.
In this article, you'll explore BGP hijacking as well as methods for detecting and approving BGP routes. The article concludes with an example policy for filtering BGP routes that you can customize to fit your requirements.
What Is BGP?
BGP is an exterior gateway protocol used to exchange routing information on an autonomous system (AS). It operates by establishing peer connections between routers in different ASs. These routers exchange routing information, which includes the list of IP address prefixes that each AS can reach. Based on this information, BGP routers build a routing table that lists all the possible paths to each network.
More on BGP:
- How BGP Selects the Best Route for Your Packets
- BGP Confederations vs. Route Reflectors and How to Choose the Right One
The primary function of BGP is to find the best path for data to travel across the complex web of networks that make up the internet. BGP uses a variety of attributes to determine the best path, including the length of the path (measured in the number of ASs the data must traverse), the reliability of the path and policy-based rules set by network administrators.
BGP is a path vector protocol, meaning it maintains the path information that gets updated as it propagates through the network. This path information helps prevent routing loops and ensures that data packets follow an efficient and loop-free path to their destination.
BGP Hijacking Basics
BGP hijacking isn't new or complex, and the consequences of a BGP hijack can be severe. Imagine your internet traffic not reaching its intended destination, or worse, being monitored or intercepted by malicious actors. These attacks can lead to data breaches, result in leaks of sensitive information and even direct users to fake websites. To make matters worse, the victim might receive responses from millions of route reflectors, advertising their path changes and exhausting their bandwidth and resources.
A BGP hijack occurs when an inaccurate route is accepted. The AS route advertises an IP route for another system so that traffic is sent to the wrong network. Because BGP lacks built-in verification, unverified IP changes can propagate to systems that accept them, leading to traffic misdirection.
How to Detect BGP Hijacking
Monitoring and security normally concentrate on malicious or overwhelming network traffic that passes into, out of and within an organization's network. Latency and misdirected traffic are viewed as problems to avoid with solid architectural choices, but slow transmission and misdirection are sometimes signs of BGP hijacking. Fortunately, tools are available to integrate relevant monitoring into your network oversight.
Configuring BGP on Equinix dedicated cloud:
- Configuring BGP with FRR on an Equinix Metal Server
- Configuring BGP with BIRD 1.6 on an Equinix Metal Server
- Elastic IPs with BGP
Use Analysis Tools to Detect BGP Hijacking
You can proactively identify potential BGP hijacking events by looking for unusual patterns, such as unexpected changes in latency, misdirected traffic or performance degradation.
Flow analysis tools can also be particularly helpful. For example, NetFlow captures IP traffic information and provides detailed network flow data, such as source and destination IP addresses, ports and protocols. Similarly, sFlow provides real-time traffic visibility by capturing packets and forwarding them to a collector for analysis. Anomaly detection systems such as BGPStream (discussed below) are also useful; these use machine learning algorithms and statistical methods to establish a baseline of normal network behavior. The systems continuously monitor network traffic against the statistical norm and identify deviations that may suggest a BGP hijacking event in real time, allowing for swift response and mitigation.
One of the major challenges of anomaly detection systems is that it's incredibly difficult for the victimized organization to track and isolate the attack traffic due to the distributed nature of BGP. Thankfully, tools and services that review routing behavior and detect suspicious activities are now available, including the following:
- BGPmon is a monitoring service designed to provide real-time alerts and analysis of BGP routing changes.
- RIPE Atlas is a global network of probes and anchors that measure internet connectivity and performance. Managed by RIPE NCC, it offers tools for network diagnostics, including traceroutes, ping tests and DNS lookups.
- RouteViews collects and archives BGP routing information around the world. This University of Oregon project offers a comprehensive view of global BGP routing tables. RouteViews can be used to study routing behavior, detect hijacking incidents and understand the propagation of BGP announcements across networks.
- BGPStream is an open source framework that offers tools and libraries to analyze BGP data in real time. It provides a platform for collecting, processing and visualizing BGP routing information from multiple data sources. BGPStream helps network admins monitor BGP activity, detect hijacking attempts and investigate routing anomalies.
Monitor BGP Announcements and Withdrawals
Monitoring BGP routing changes can help you identify cues that may indicate a BGP hijacking event.
When an AS announces a new route, it tells the entire internet how to reach certain IP address blocks. Route withdrawals signal that a particular path is no longer available. Monitoring these activities can help you spot unauthorized changes to a route that you depend on or control.
BGPmon can be helpful here as well. The service continuously monitors BGP announcements and withdrawals and can notify administrators about unauthorized route advertisements.
How to Prevent BGP Hijacking
The best solution to prevent BGP hijacking would be for all ISPs to implement authorization and encryption for BGP routing transactions and to monitor and repair inaccurate routing changes. If your ISP does not implement sufficient security controls to safeguard BGP, there are steps you can take to protect your network.
Use Resource Public Key Infrastructure
Resource Public Key Infrastructure (RPKI) authenticates BGP route announcements and withdrawals. To use RPKI, network operators must first obtain digital certificates from a trusted certificate authority (CA). These certificates bind IP address blocks to their rightful owners, creating a chain of trust. The CA issues Route Origin Authorizations (ROAs), which specify which ASs are authorized to originate from certain IP prefixes. Once ROAs are in place, network operators can configure their BGP routers to validate incoming route announcements against the RPKI database. This involves checking the ROAs to ensure that the AS advertising a particular IP prefix is indeed authorized to do so. If the validation fails, the route is rejected or deprioritized, preventing hijacked or unauthorized routes from being accepted. Prefix lists also offer a layer of protection in BGP filtering; they're used to match specific IP prefixes and apply actions such as permit or deny.
To implement RPKI validation, network operators typically use specialized software known as RPKI validators. These validators download and verify ROAs from multiple CAs, maintaining an up-to-date repository of valid route authorizations. The validated data is then fed into BGP-enabled routers, which use it to make informed routing decisions.
RPKI can also be used to authenticate route withdrawals. When a network operator withdraws a route, the RPKI system can verify that the withdrawal request is legitimate, ensuring that malicious actors cannot disrupt network traffic by falsely withdrawing routes.
Configure BGP Sessions to Only Accept Legitimate Routes
Strict filtering policies can help prevent BGP hijacking by limiting the advertised routes and withdrawals that your network will process. Two effective methods are prefix filtering and AS path filtering. Prefix filtering specifies which IP prefixes are allowed to be advertised or received. Defining a list of legitimate prefixes lets you accept only authorized routes and can prevent the acceptance of malicious or incorrect routes that could lead to BGP hijacking. AS path filtering lets you create regular expressions to match specific AS paths you confirm are legitimate. Filtering based on AS paths prevents routes from untrusted or suspicious ASs from being accepted and lowers the risk of BGP hijacking.
Route maps apply granular control over which routes are accepted or advertised. These maps, less formally called BGP policies, set conditions like prefix length, origin or AS path. This combination of conditions creates a strong, layered filtering setup, limiting the potential to process inaccurate routes.
An Example BGP Policy
The following BGP route map incorporates a combination of filters to create a strong policy. Each row in the following table is a specific rule that explicitly accepts or limits the BGP route information that this network will accept.
The fields of this policy are expressed in a human-readable, consistent format. The only exception is "Policy Name," which provides a descriptive name that is not significant for routing. The "Action" column specifies whether the rule permits or denies the route, "Prefix/AS Path" indicates the IP prefix or AS path to which the rule applies and "Description" provides additional context or rationale for the rule.
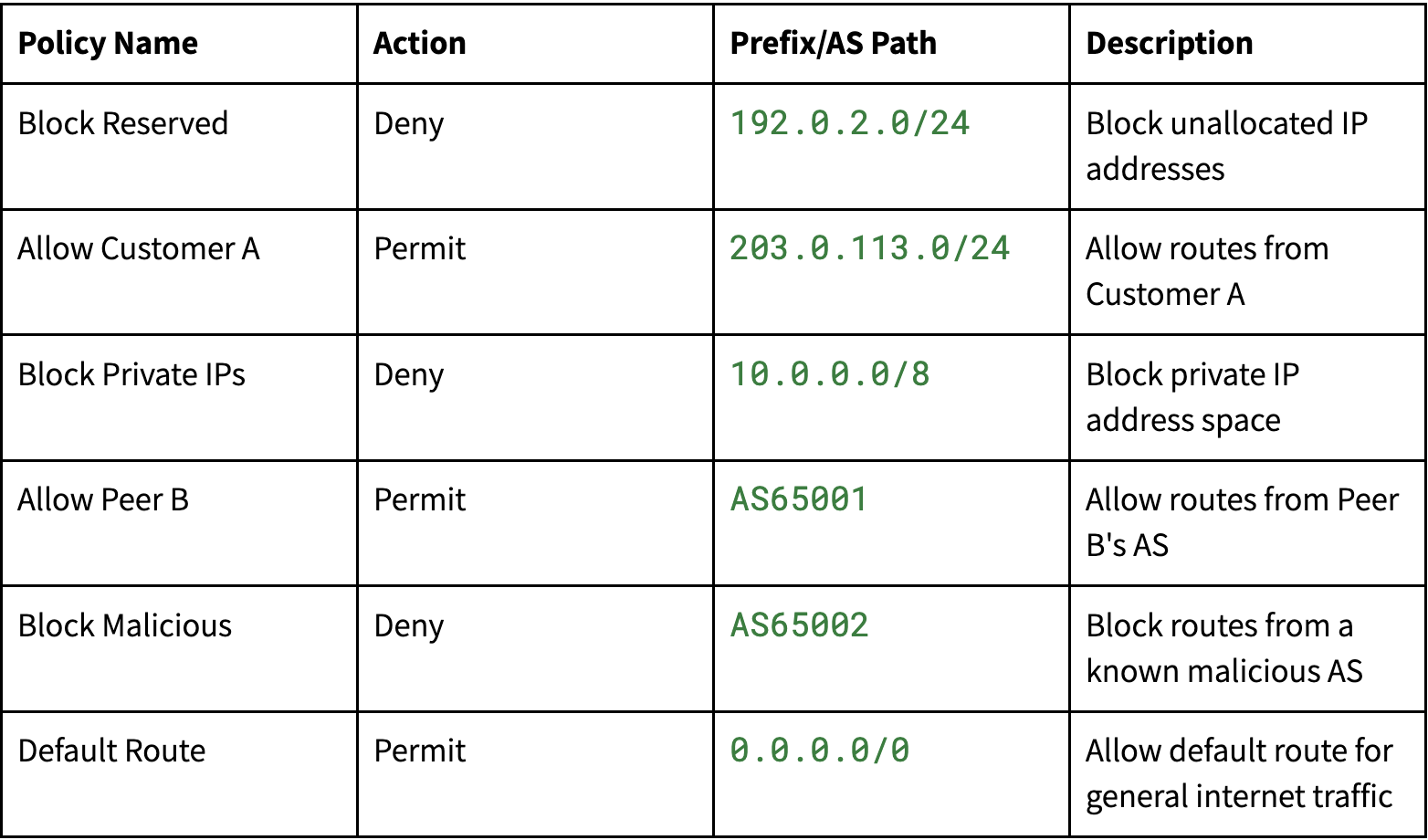
In this example, the "Block Reserved" policy denies routes for unallocated IP addresses, which are often used in malicious activities. The "Allow Customer A" policy permits routes from a specific customer. The "Block Private IPs" policy prevents private IP address spaces (the reserved 10.0.0.0/8 space) from being advertised since those IPs shouldn't appear on the public internet.
Conclusion
BGP is essential for internet traffic routing, but its design makes it vulnerable to manipulation that leads to numerous hijacking attempts. The telco incident we described in the beginning of the article highlighted how small errors can escalate into significant issues.
The risks associated with inadequate BGP security measures will continue to persist if effective defenses are not put into place. Proactive monitoring, proper security protocols and swift incident response can mitigate these risks. Tools like NetFlow, sFlow, anomaly detection systems and specialized BGP monitoring services can help you identify and respond to hijacking attempts. Moreover, adopting RPKI and BGPsec, strict filtering policies and route validation are small investments that can greatly improve the resilience of your BGP implementations. Ensuring proactive security in routing management is also crucial for the stability, reliability and trustworthiness of the global network and your own organization's network.